Managing Domain Password Policy in the Active Directory
To protect user accounts in the Active Directory domain, an administrator must configure and implement a domain password policy that provides sufficient complexity and length of a password as well as the frequency of changing of user and service account passwords. Thus, you can make it hard for an attacker to crack user passwords using the brut force attack, or capture a passwords when send over a network.
By default, to set common requirements for a user passwords in the AD domain the group policy settings (GPO) are used. The password policy of the domain user accounts is configured in the Default Domain Policy.
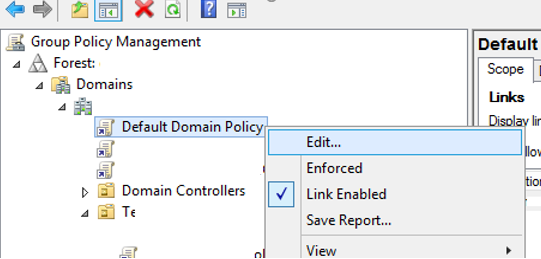
- To configure the AD account password policy, open the Group Policy Management console (gpmc.msc);
- Expand your domain and find the GPO named Default Domain Policy. Right-click it and select Edit;
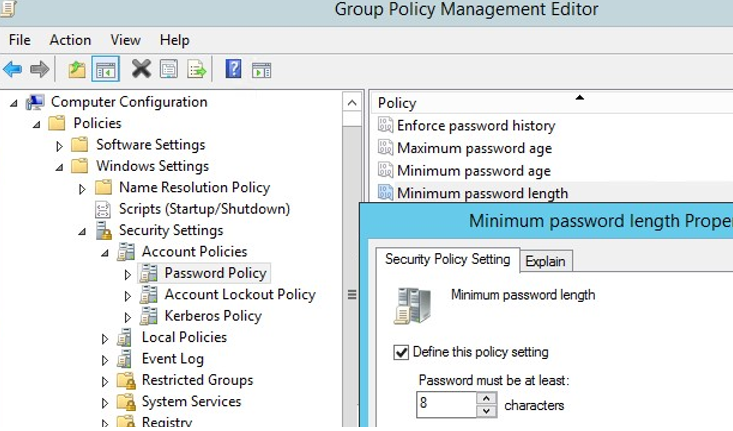
- Password policies are located in the following GPO section: Computer configuration-> Windows Settings->Security Settings -> Account Policies -> Password Policy;
- Double-click a policy setting to edit it. To enable a specific policy setting, check the Define this policy settings and specify the necessary value (on the screenshot below, I have set the minimum password length to 8 characters). Save the changes.
- The new password policy settings will be applied to all domain computers in the background in some time (90 minutes), during computer boot, or you can apply the policy immediately by running the
gpupdate /forcecommand.
Let’s consider all available Windows password settings. There are six password policies:
- Enforce password history – determines the number of old passwords stored in AD, thus preventing a user from using an old password;
- Maximum password age – sets the password expiration in days. After the expiration of this period, the system will prompt a user to change the password. This policy ensures that users regularly change the password;
- Minimum password length – it is recommended that passwords should contain at least 8 symbols (if you specify 0 here, the password is not required);
- Minimum password age – sets how often users can change their passwords. This setting won’t allow the user to change the password too often to get back to an old password they like by removing them from the Password History log after the password has been changed several times in a row. As a rule, it is worth to set 1 day here in order users can change a password themselves if it gets compromised (otherwise an administrator will have to change it);
- Password must meet complexity requirements – if the policy is enabled, a user cannot use the account name in a password (not more than 2 symbols of a
usernameorFirstnamein a row), also 3 types of symbols must be used in the password: numbers (0–9), uppercase letters, lowercase letters and special characters ($, #, %, etc.). Also, to prevent using weak passwords (from the password dictionary), it is recommended to regularly audit user passwords in the domain. - Store passwords using reversible encryption – user passwords are stored encrypted in the AD database, but in some cases you have to grant access to user passwords to some apps. If this policy setting is enabled, passwords are less protected (almost plain text). It is not secure (an attacker can get access to the password database if the DC is compromised; an read-only domain controllers (RODC) can be used as one of the protection measures).
In additional, the following settings should be configured in the GPO section Account Lockout Password:
- Account Lockout Threshold – the number of failed sign-in (attempts to enter a wrong password) can be made by user prior to the lockout of his account;
- Account Lockout Duration – how long an account will be locked, if the user has entered the wrong password several times;
- Reset account lockout counter after – the number of minutes after which the Account Lockout Threshold counter will be reset.
If the specific domain account is locked out too often, you can identify the source of account lockouts using this method.
The default settings of password policies in the AD domain are listed in the table below:
| Policy | Default value |
| Enforce password history | 24 passwords |
| Maximum password age | 42 days |
| Minimum password age | 1 day |
| Minimum password length | 7 |
| Password must meet complexity requirements | Enabled |
| Store passwords using reversible encryption | Disabled |
| Account lockout duration | Not set |
| Account lockout threshold | 0 |
| Reset account lockout counter after | Not set |
You can check the current AD password policy settings on any domain computer using the gpresult command.
Any AD domain can have only one password policy applied to the domain root (there are some nuances, but we’ll talk about them later). Usually, a domain password policy is configured in the GPO named Default Domain Policy. If you create another GPO with different password settings and apply it to the specific OU, its settings will be ignored. The domain controller, the owner of FSMO’s PDC Emulator role, manages the domain password policy. To edit Default Domain Policy settings, you must have the domain administrator privileges.
The password policy GPO settings are applied to all domain computers (not users). If you need to create separate password policies for different user groups, you must use the Fine-Grained Password Policies that appeared in the AD version of Windows Server 2008. Granular password policies allow to set increased length or complexity of passwords for administrator accounts (check out the article Securing administrator accounts in AD domain), or make passwords of some accounts more simple or even disable them completely.
In a workgroup, you will have to configure password policies on each computer using the local GPO editor – gpedit.msc, or you can transfer the local GPO policy settings between computers using this method.